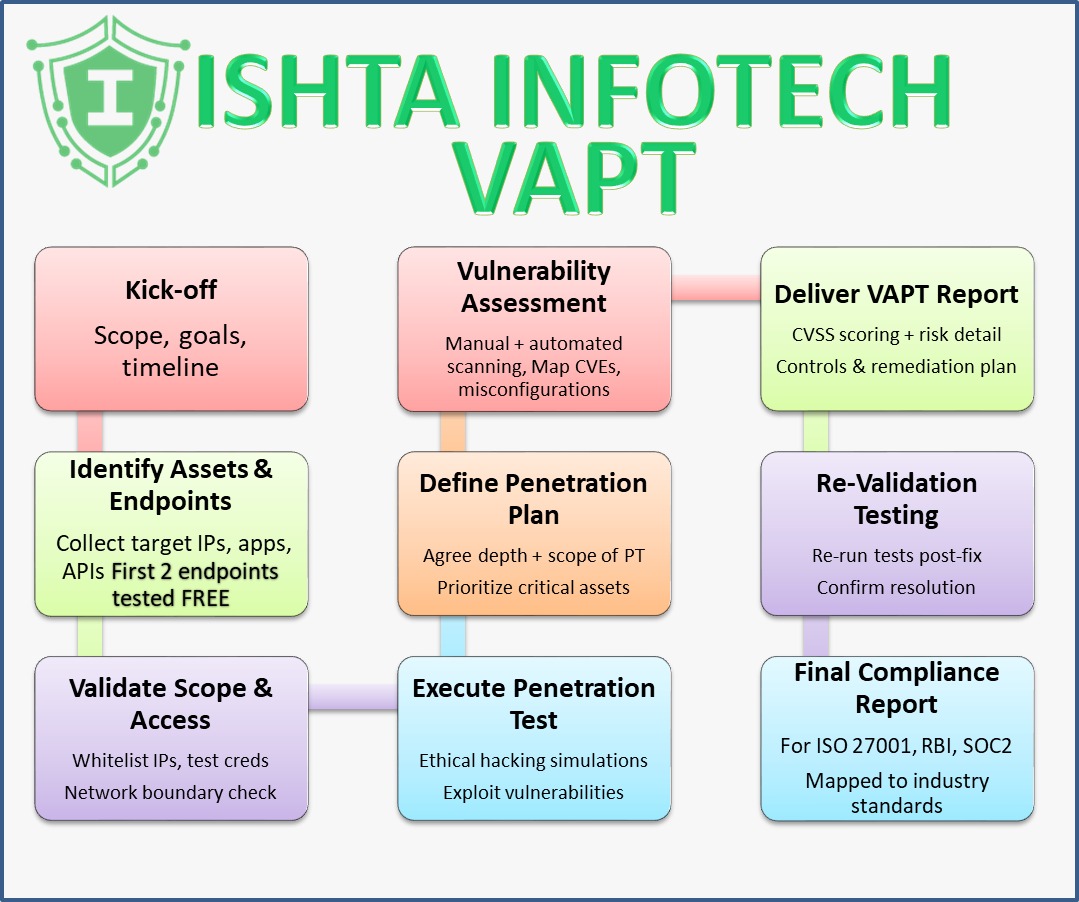
Our structured VAPT process ensures thorough assessment and reporting to secure your digital assets effectively.
Vulnerability Assessment (VA)
Comprehensive Analysis
Using CVSS and expert tools to find weaknesses in systems and applications.
CVSS Scoring
Quantifies severity and helps prioritize remediation efforts based on score.
Automated + Manual Testing
Thorough analysis across networks, apps, and systems using hybrid techniques.
Vulnerabilities by CVSS Score
Benefits of CVSS Scoring
- Prioritization of remediation efforts
- Effective risk management
- Efficient resource allocation
Why Choose ISHTA INFOTECH for VA?
- Expert cybersecurity professionals
- Comprehensive assessments
- Use of CVSS framework
- Actionable remediation recommendations
Penetration Testing (PT)
Simulate real-world cyber-attacks to uncover exploitable vulnerabilities in your systems.
Network & Internal Testing
Simulate attacks from both inside and outside the network perimeter.
Web App Testing
Check for SQL injection, XSS, and OWASP Top 10 vulnerabilities.
Social Engineering
Human-focused testing including phishing simulation and password policies.
Exploitation & Reporting
Attempted exploitation and detailed reporting of real-world threats.
Standard Pen Testing Approach
- Planning
- Discovery
- Attack
- Analysis
- Reporting
We follow OWASP guidelines to assess web apps for common threats like XSS, SQLi, and security misconfigurations.
Types of Penetration Testing
Network Infrastructure Testing
We analyze internal and external networks for exploitable vulnerabilities and provide actionable recommendations to mitigate security risks.
Cloud Penetration Testing
Tailored cloud testing to discover misconfigurations and weaknesses in cloud-based environments like AWS, Azure, or GCP.
Wireless Testing
Identify and secure open entry points in wireless networks to prevent unauthorized access and data breaches.
Web Application Testing
Scan and exploit vulnerabilities in web apps including SQL injection, XSS, CSRF, and more—aligned with OWASP standards.
Social Engineering
Simulate phishing and manipulation tactics to evaluate employee awareness and your organization's social defense posture.
Mobile Security Testing
Assess mobile apps for logic flaws, API weaknesses, and code-level risks to ensure device and data integrity.
Why Choose ISHTA INFOTECH for PT?
- Real-world attack simulations
- OWASP-compliant methodology
- Actionable security insights
- Customized testing aligned to your infrastructure
Ready to Strengthen Your Cybersecurity?
Let ISHTA INFOTECH help you identify and fix vulnerabilities before attackers do. Our experts are just a click away.
Reach Us